Responding to North Korean Cyberattacks
Ji Min Park1, Neil C. Rowe2, Maribel Cisneros3
1Republic of Korea Air Force, Seoul, Republic of Korea
2U.S. Naval Postgraduate School, Monterey, California, USA
3U.S. Army, Washington, DC, USA
kimhkmin@naver.com
ncrowe@nps.edu
maribel.cisneros.mil@mail.mil
Abstract: North Korea has engaged in repeated cyberattacks on South Korea in the last ten years. These are consistent with their other provocations such as their nuclear weapons programs and aggressive activities along the border. The damage of these attacks is increasing, and they are a significant annoyance that is preventing progress on resolving the conflict between the two states. This paper will first survey the dramatic differences between North Korea and South Korea in cyberspace, and summarize the continuing evolution of North Korean cyberattacks. Attribution of most attacks to North Korea is not difficult because many of the same methods are used repeatedly, and many of the attacks are timed to coincide with important anniversaries. Thus, unlike with cybercriminals, these cyberattacks can often be predicted and recognized, and preparations can be made for them. North Korean cyberattacks often violate international law since they indiscriminately target civilians since the state considers itself not subject to international law. Nonetheless, there are many things South Korea can do to respond. International law can be invoked even without cooperation by the parties, and sanctions can be imposed. Defenses can be strengthened by better coordination of defenses between the private and governmental sectors through a unified early-warning defense. Repeated cyberattacks also justify a counterattack according to international law. North Korea has a limited set of state-mandated software on a small set of networks, and this makes widespread effects of cyberattacks on them quite possible. The main difficulty is getting access to these networks, but there are ways, especially given the growing use of smartphones in North Korea. As for attack goals, what North Korea fears the most is information about the rest of the world getting to their citizens, so sending accurate such information should be a major goal of cyber-counterattacks -- data destruction is unnecessary.
Keywords: North Korea, cyberattacks, response, attribution, defense, offense, international law
This paper appeared in Proc. 15th European Conference on Cyber Warfare and Security, Munich, Germany, July 2016.
1. Introduction
The two Koreas are divided by ideological issues and have had a hostile relationship since 1950. Since the 2000s, North Korean provocations have shifted to cyberspace and to what they call “psychological operations” (Hewlett-Packard Security Research, 2014). These provocations attempt to express their political will and create a favorable environment for negotiation. Typically, North Korean official media first makes critical statements, then conducts cyberattacks, and then possibly conducts armed provocations. If South Korea could plan good responses to North Korean cyberattacks, North Korea might stop their provocations before they escalate. Good defensive and offensive countermeasures to cyber provocations can help reduce threats and prevent needless damage. However, it is important to find appropriate responses in cyberspace, a domain for which countries have limited experience (Lee et al, 2015; Park, 2015).
2. Cyberattacks on South Korea
2.1 Korean cyber capabilities
North Korea has separate domestic intranets for citizens, the Ministry of People’s Security, the Ministry of State Security, and the military. The unclassified intranet “Kwangmyong” connects 3,700 organizations with 50,000 estimated users. Most North Korean computers use the locally developed operating system Red Star, based on open-source Linux software and thus subject to the usual vulnerabilities of Linux (Lee, 2011). To connect to the Internet, optical-fiber cables link from China and use Chinese IP addresses. Use of the Internet in North Korea is strictly controlled by the North Korean government, and users are estimated to be only hundreds of high-ranked officials. Furthermore, operating hours are limited because an electrical power shortage. It was significant progress when they opened six official Web sites to the public. Cellular networks provide 3G-network cellphone service, and the number of users is estimated at 2.5 million, 10% of the population. Though general users cannot access the Internet, it can be reached from the cellular network (Mansourov, 2014).
Attacks directly from North Korea are easy to attribute because they have few IP addresses (Lim et al., 2013). So North Korea usually launches attacks from elsewhere, especially China. Since there are no voluntary hacker groups in North Korea because the government strongly controls all networks, all cyberattacks coming directly or indirectly from North Korea can be attributed to the North Korean government (HP Security Research, 2014). However, because of economic sanctions, North Korea has had difficulty in acquiring technologies and devices for developing their cyber capabilities.
On the other hand, South Korea has the 12th highest number of Internet users in the world, and depends considerably on the Internet, maintaining high Internet availability (MSIP and KISA, 2014). In South Korea, 98% of businesses with more than 10 employees are connected to the Internet, and 86.7% of employees are using the Internet for business. In addition, most citizens have smartphones using 4G technology. South Korea is connected to the Internet via a 27 Tbps connection through undersea cables and communication satellites. In 2014, South Korea had 122 million IPv4 addresses, which is the 6th highest rank in the world, and had 1018 Autonomous System (AS) numbers as the 13th rank. The national Domain Name Service (DNS) consists of 15 sites, and its average daily query total is about 1.6 billion. Internet services are provided by a number of private Internet Service Providers. South Korea uses many applications popular around the world such as Microsoft Office or Adobe Photoshop, but many South Koreans prefer to use domestic word processors and domestic antivirus software. Furthermore, due the policy of favoring domestic software manufacturers, government organizations tend to use domestic products.
South Korea’s large cyber resources and dependency on digital culture are a disadvantage in cyberwarfare (Kshetri, 2014) since so many potential targets exist in its extensive cyberspace (Lim et al., 2013). In addition, it is hard for the South Korean government to control its country’s cyberspace because much of it is in the private sector, and role division between organizations is not always settled (Boo, 2013). South Korea also provides diverse electronic-government services which are a tempting target in cyberwarfare because they have much personal information.
2.2 Cyberattacks from North Korea against South Korea
North Korea has said it is preparing for “fourth generation warfare” by establishing cyberwarfare units and developing capabilities (IUE, 2014). More than 70,000 cyberattacks have been conducted against South Korean government and civilian Web sites, and many of these have been attributed to North Korea (Chae, 2013). Some of the most serious attacks have been:
· On June 10, 2004, South Korea government sites were attacked by malware that appeared to be coming from China (Kim, 2010). According to statistics, among 301 damaged computers, 222 devices belonged to the government and 79 to private companies and universities. Based on the analysis, the origin of the attack was China, but the IP addresses were Chinese ones being leased by North Korea. Secret information related to national security was leaked for six months (Chae, 2013). In addition, North Korea accessed South Korean military wireless-communication networks (HP Security Research, 2014).
· North Korea penetrated South Korea’s military communication channel in 2005 during Ulchi Focus Lens, the annual combined military exercise with the United States (Ventre, 2011).
· The U.S. State Department was attacked by unknown entities in cyberspace in June 2006 (HP Security Research, 2014). Although detailed information is not available, the South Korean military reported that North Korea’s Unit 121 was implicated in this attack.
· In March 2007, the Korean Army and the National Institute of the Environment were attacked (Mansourov, 2014). After the hackers obtained certificate passwords, they stole information related to chemical-accident response. South Korea’s government announced that the malware was from a foreign country, and it could have been from North Korea (Lee, 2009).
· North Korea in 2008 sent malicious emails with Trojan Horses to the South Korean military, and social engineering attempts such as spear phishing were also identified (Ventre, 2011).
· July 2009 saw a distributed denial-of-service (DDoS) attack targeting 21 Web sites, including government sites, media, and financial institutions. Hackers used sophisticated methods such as automatic deletion of source files and destruction of zombie hard disks to hide evidence of the attacker’s identity (Chae, 2013). The attack exploited over 400 servers in the world to make tracing hard. The total number of bots was approximately 20,000 devices. Among them, 12,000 infected computers were located in South Korea, and others were in foreign countries (Mansourov, 2014).
· In 2010, several cyberattacks for information leakage were targeted against South Korean military officers via malware (Ventre, 2011). In July, there were DDoS attacks against several government sites (Mansourov, 2014) conducted by the same botnets used in 2009 and the signatures of the malware were the same (Jung, 2010).
· In January 2011, Free North Korea Radio was attacked by North Korea. Unusually, this attack came from North Korea directly, which indicated that they wanted the attack to be attributed.
· In March 2011, a large DDoS attack was conducted against the South Korean government and private services. Over 700 servers and 100,000 infected PCs were mobilized (Chae, 2013). The attack was similar to previous attacks known to be from North Korea (Ahn, 2013) and used illegal game sites to spread malware that infected PCs and set up botnets (Mansourov, 2014).
· In April 2011, the South Korean bank Nonghyeop was hacked and their banking service was paralyzed for several days (Chae, 2013). The South Korean prosecutor said that this attack was conducted by North Korea’s RGB after seven months of preparation (Park, 2011).
· In June 2012, North Korea attacked the Web site of Joongang Ilbo, a conservative press company (Mansourov, 2014). The South Korean Cyber Terror Response Team in the National Police Agency reported that the IP addresses of this attack were related to the North Korean Ministry of Posts and Telecommunications (Park, 2013). Databases related to news articles and pictures were destroyed by this attack.
· In March 2013, North Korea attacked PCs, servers, and automated teller machines of six broadcast companies and financial institutes, causing deletion of data and service interruptions (Chae, 2013). This attack was an advanced-persistent-threat attack similar to the Nonghyeop hacking in 2011 (Boo, 2013). This attack was prepared over eight months, and approximately 57,000 PCs and servers were damaged (Lee, 2015). IP addresses belonging to North Korea were identified 13 times, and many intermediate pathways used were identical to their past attacks. In addition, 30 types of malware among the total 76 instances of malware used for this attack were used in previous North Korean attacks (HP Security Research, 2014).
· In April 2013, the international hacking group Anonymous attacked North Korea’s networks (HP Security Research, 2014). Apparently in response, malicious smartphone applications spread as free games infected approximately 20,000 devices in South Korea from May to September (Mansourov, 2014).
· In June 2013, a DDoS attack was attributed to the DarkSeoul hacking group related to North Korea’s Lab 110 (HP Security Research, 2014). The malware used stolen passwords and destroyed hard drives (Lee, 2015).
· In 2014, Sony Pictures Entertainment was attacked apparently in response to the film The Interview, which depicted the assassination of a North Korean leader (HP Security Research, 2014). The US FBI attributed this cyberattack to North Korea and concluded that the attack was malware that both stole information and destroyed data (FBI, 2014). Experts have estimated the damages were up to $100 million (Richwine, 2014).
· In December 2014, Korea Hydro and Nuclear Power Co., Ltd (KHNP) was hacked, and the South Korean Public Prosecutor’s Office claimed North Korea as the source based on traces of IP addresses that belonged to North Korea (Kim, 2015).
Figure 1 shows the monthly trends in cyberattacks 2004-2015. Many attacks occurred in March, April, and July. In March there is an annual large-scale combined military exercise involving South Korea and the United States; apparently cyberattacks are intended to protest and disturb the exercises. June 25 is the anniversary of the start of the Korean War, and July 4 is the U.S. Independence Day. These coincidences suggest that North Korea is involved in attacks in those months.
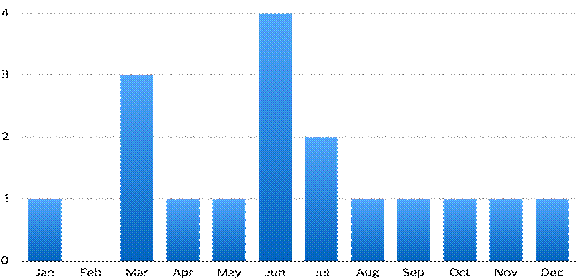
Figure 1: Monthly Statistics of North Korea’s Major Cyberattacks from 2004 to 2015
From 2004 to 2008, most attacks were information-gathering from government and research agencies. Since 2009 there have also been DDoS attacks against the private sector such as media and financial institutes. Hackers have increasingly targeted groupware and antivirus systems, and damages have increased. In addition, in December 2014, they hacked the KHNP, part of the national infrastructure. So the targets of North Korea’s cyberattacks have shifted from intelligence collection to DDoS attacks, and then to advanced persistent threats on the private sector. The increasing scope of these attacks means that a lethal cyberattack from North Korea is increasingly possible.
2.3 Attribution of the cyberattacks
How do we know that the abovementioned attacks were from North Korea? Attribution can be done by many methods (Rowe, 2015, “Attribution”). Data analysis that indicates similarities between attacks is one way. For instance, (Seo, Won, and Hong, 2011) compared the July 2009 and March 2011 attacks by inspecting the traffic initiated from infected systems at the Pohang University of Science and Technology. They found that both attacks (1) were autonomous with a predefined target list and start date and time; (2) used botnets with low-rate (54.2kbs) attacks to remain undetected on the infected hosts; (3) used multiple forms of DDoS attacks (TCP SYN floods, ICMP floods, UDP floods, and HTTP GET/POST flood); and (4) included instructions on the bots to delete documents and corrupt the Master Boot Record. These similarities are beyond chance.
The U.S.-Computer Emergency Response Team (U.S. CERT, 2013) determined that the code in the March 2013 attacks was designed to avoid South Korean antivirus signatures similarly to the two abovementioned attacks. FireEye analysts corroborate the U.S.-CERT assessments for this particular attack (Pidathala, Khalid, Singh, and Vashisht, 2013) and found that the malware could also disable the popular AhnLab South Korean antivirus software by issuing a taskkill command for it. The code was to be “dropped” by another program, which could have been over HTTP as there was an increase of executable HTTP downloads a month before the attacks (Dell SecureWorks, 2013). This basic attack method is mentioned in the World War C report about North Korea: hacking websites with malware to take over their operating system and disable their antivirus software (Geers et al, 2013). McAfee assessed that the same group has been behind all the cyberattacks against South Korea since 2009. (Sherstobitoff and Liba, 2013) concluded these attacks to be related because it was mostly the same code using the same password for the zip files, with some added functionality such as file extraction in later versions. Symantec has also linked cyberattacks against South Korea since 2009 to include the June 2013 attack (Symantec, 2013).
It is also clear that South Korea has been the primary target of these attacks because of their dates, their attempts to evade specific South Korean antivirus software, and their target lists of South Korean organizations and Korean-military search terms. The autonomous nature of the attacks also points to North Korea which has limited Internet connections for command-and-control. Most of the infected bots were in South Korea (Seo et al, 2011), which suggests North Korea’s involvement since they have repeatedly attempted to grow botnets in South Korea by infected games, phishing attacks, and HTTP executables. The code also tried to extract military files of special interest to North Korea. Moreover, the increased level of malware sophistication and added functionality with each attack are consistent with organized military cyber units that continue to develop their skills.
3. Possible Responses to North Korean Cyberattacks
3.1 Legal responses
Although North Korea has been termed a “rogue state” because it often ignores international law, the international community can affect it through sanctions (Cisneros, 2015). South Korea can invoke Articles 39, 41, and 42 of the U.N. Charter (1945), present collected evidence to the U.N. Security Council, and ask them to take action against North Korea. Under Article 39, the Council will evaluate the evidence and determine if “the existence of any threat to the peace exits, breach of the peace, or act of aggression” and “what measures shall be taken in accordance with Article 41 and 42.” The Council will attempt to settle the dispute without the use of armed force, and if that fails to stop the threat, it could authorize South Korea to use military operations to maintain or restore peace.
Responding to cyberattacks involves a significant amount of time and resources, and requires response personnel to have technical knowledge. South Korea can sue North Korea for damages through the International Court of Justice (ICJ) which enforces customary international law (ICJ, 2015). The ICJ can then review the evidence, conduct investigations, and issue their ruling, which North Korea, as a signatory of the U.N. Charter, is mandated to abide by (ICJ, 2015). Even a single attack can be sufficiently damaging that the perpetrators can be held accountable for monetary damages. That is, the ICJ can enforce tort law, which stipulates that if an aggressor conducts an intentional act to cause harm, the victim can pursue a lawsuit to obtain compensation; cyberspace torts are classified as intentional torts (Grama, 2010).
North and South Korea are still legally at war so cyberattacks between them also need to abide by the law of armed conflict. The basic principles are distinction, proportionality, military necessity, and humanity (Carr, 2011). Since North Korean systems are tightly controlled by their government, targeted cyber-counterattacks on North Korean computer systems will be a direct attack on their military and government systems, which will abide by the principle of distinction of only targeting combatants. The counterattacks also can easily meet the proportionality criteria, as there is not much to attack. The counterattacks can also meet the military-necessity criteria, as the cyberattack will seek to only “weaken the military forces of the enemy” (ICRC, 2002). Additionally, such attacks can be consistent with the humanity principle because they can avoid unnecessary suffering and injuries by attacking only cyberspace.
Since we have strong evidence that North Korea is responsible for many attacks on South Korea, the U.N., through the ICJ, can subpoena packet information between these two states to facilitate accountability after a cyberattack. The U.N. will need international cooperation to obtain information from the different traversed routers. The broad perspective of the U.N. can take into account non-cyber issues such as the possibility of war in the Korean Peninsula, maintaining peace talks, handling North Korea’s established military objective to reunite the Koreas, and addressing North Korea’s inability to feed their citizens without international aid (Worden, 2008). Previous cases have shown that if state-sponsored attacks continue to go unpunished, civilian organizations will continue to be targeted.
3.2 Defensive countermeasures
A defender is not powerless in cyberspace (Singer and Friedman, 2014). Cyber-defensive countermeasures are possible based on the idea of active defense (Harrington, 2014) and these can be used by South Korea. Beaconing transmits current user information, such as IP addresses, when the stolen file is opened to enable tracing of the theft. Honeypots are systems designed solely to collect information about attacks (Harrington, 2014) and can be effective against distributed denial of service, malware installation for advanced persistent threats, and other kinds of attacks. Sinkholing intercepts malicious traffic from botnet clients by masquerading as one of its command-and-control servers (Harrington, 2014), and can thereby foil botnets.
Attackers can choose a type, time, and target of attack, but they must subvert all protective layers to make their attack successful. This means a cyber early-warning system can work well and provide a wider viewpoint to defense since it only need recognize some clues to an attack (Robinson, Jones, and Janicke, 2015). A good cyber early-warning system should provide information about the current situation, the attacker, the targets, and the attack methods (Golling and Stelte, 2011). Cyberattacks motivated by political issues usually have five phases: latent tension, cyber reconnaissance, an initiating event, cyber mobilization, and a cyberattack (Carr, 2011). That suggests that defense should start collecting a good deal of cyber data in the early phases. Early information about subject, target, and method could be incorrect, but immediacy is more important than accuracy because it aids a quick defense. An early-warning system should also share threat information quickly between systems, and it is especially important to get warnings to critical infrastructure such as power plants and water-supply plants. Furthermore, since North Korea has exploited antivirus software to spread malware, cooperation with foreign cyber-security companies is also important.
3.3 Offensive countermeasures
South Korea can also try to counterattack North Korea since that is justified by the law of armed conflict as discussed above. Despite the many air-gapped systems in North Korea, such systems are hard to update and can have persistent vulnerabilities. Brittleness of enemy systems can be demonstrated by the ability to hack into enemy systems at any time as a kind of “retaliatory hacking” (Libicki, 2013; Harrington, 2014). Counterattacks can be quite limited, as a form of coercion (Flemming and Rowe, 2015) or a show of force to encourage North Korea to cease cyberattacks and offer compensation. Joint coercion with conventional military operations can also enhance bargaining power and prevent escalation.
When attribution of a cyberattack is easy to prove, South Korea could consider targeting the originating sites of the cyberattack as a simple way to satisfy the principle of proportionality (Rowe, 2015, “Distinctive”). Second, because the North Korea government strongly controls information about the outside world in violation of human rights (IUE and Ministry of Unification, 2014), their propaganda services make good targets. A good counterattack need not harm North Korea at all, just provide accurate information about the outside world on their intranets, since the North Korean government fears this information so much. Distributed denial-of-service attacks based on botnets are also possible against North Korea (Radunovic, 2013). The estimated cost of a distributed denial of service botnet that could attack national-level targets is only 6,000 euros.
Collateral damage, difficulties of damage localization of cyber weapons, and direct damage from cyberattacks could be redeemed to a certain degree by using reversible counterattacks (Rowe, 2010). Reversibility can be achieved using encryption attacks, obfuscating attacks, withholding-information attacks, or resource-deception attacks (Rowe, 2010). Damage cannot always be recovered fully in some cases such as time-sensitive operations, and reversibility is less possible as time goes on and adversaries attempt to stop the counterattack. But if attackers provide recovery or assume responsibility for most of the damages, criticism of the counterattack could be reduced.
One concern with counterattacks is the possibility of escalation of the conflict. But considering North Korea’s limited Internet infrastructure, North Korea can only accomplish attacks if they are planned well in advance. If South Korea counterattacks it, the North Korean government should not be able to counter-counterattack quickly, particularly if the counterattack targets are intended for supporting attacks. And attacks on the North Korean government’s propaganda services should not affect the North Korean public. Thus the risk of escalation with direct counterattacks is relatively less than those of viruses, worms, or other methods with hard-to-predict results.
4. Conclusion
The extensive infrastructure and diversity of South Korea makes cyberattacks an appealing option for North Korea. The last ten years have seen many such attacks, most of which were easy to attribute. But South Korea has many options in response. More legal measures are possible. A better coordinated defensive strategy is important, combining government and the private sector. Several kinds of offensive measures could be useful, and they do not need to destroy anything to be powerful.
Disclaimer
The views expressed are those of the authors and do not represent the Government of the Republic of Korea or the U.S. Government.
References
Ahn, Y. (2013) “Study of Development Plan for National Defense System against Cyberattacks,” Review of the Korea Institute of Information Security and Cryptology, Vol. 23, No. 2, pp. 48–54 (in Korean).
Boo, H. (2013) “Issue of Cyber Security and Policy Directions: Discussions for the Establishment of the Defense Ministry’s Cyber Policy,” Journal of National Defense Studies, Vol. 56, No. 2, pp. 97–122 (in Korean).
Carr, J. (2011) Inside Cyberwarfare (2nd ed.), O’Reilly Media, Sebastopol, CA, US.
Chae, J. (2013) “The Changing Security Environment and Cyber Security,” The Journal of Political Science and Communication, Vol. 16, No. 2, pp. 171–193 (in Korean).
Cisneros, M. (2015) Cyber-Warfare: Jus Post Bellum, Master’s thesis, Naval Postgraduate School, Monterey, CA, US, March.
Dell SecureWorks (2013, March 21) “Wiper Malware Analysis Attacking Korean Financial Sector, retrieved from www.secureworks.com/cyber-threat-intelligence/threats/wiper-malware-analysis-attacking-korean-financial-sector/.
Federal Bureau of Investigation (FBI) National Press Office (2014) “Update on Sony Investigation,” retrieved from www.fbi.gov/news/pressrel/press-releases/update-on-sony-investigation?utm_campaign=email-Immediate&utm_medium=email&utm_source=national-press-releases&utm_content=386194.
Flemming, D, and Rowe, N. (2015) “Cyber Coercion: Cyber Operations Short of Cyberwar,” Proceedings of the 10th International Conference on Cyberwarfare and Security ICCWS-2015, Skukuza, South Africa, March, pp. 95–101.
Geers, K., Kindlund, D., Moran, N. and Rachwald, R. (2013) “World War C: Understanding Nation-State Motives behind Today’s Advanced Cyberattacks,” retrieved from www.fireeye.com/resources/pdfs/fireeye-wwc-report.pdf.
Golling, M., and Stelte, B. (2011) “Requirements for a Future EWS - Cyber Defence in the Internet of the Future,” Proceedings of the 3rd International Conference on Cyber Conflict, Tallinn, Estonia, pp. 1-16.
Grama, J. (2010) Legal Issues in Information Security, Jones and Bartlett Learning, Sudbury, MA, US.
Harrington, S. (2014) “Cyber Security Active Defense: Playing with Fire or Sound Risk Management?,” Richmond Journal of Law and Technology, Vol. 20, No. 4, pp. 1-41.
Hewlett-Packard (HP) Security Research (2014) Profiling an Enigma: The Mystery of North Korea’s Cyber Threat Landscape (HP Security Briefing Episode 16). Retrieved from community.hpe.com/hpeb/attachments/ hpeb/off-by-on-software-security-blog/388/2/HPSR%20SecurityBriefing_Episode16_NorthKorea.pdf
Hong, S. (2011) “North Korea’s Cyberattack Methods, Advanced and Intelligent,” The Unified Korea, Vol. 328, pp. 34–35 (in Korean).
Institute of Unification Education (IUE) and Ministry of Unification, South Korea (2014) Understanding North Korea 2014, Nuel-Pum Plus, Seoul, South Korea.
International Committee of the Red Cross (ICRC) (2012) “International Humanitarian Law: Answers to Your Questions,” retrieved from www.redcross.org/images/MEDIA_CustomProductCatalog/ m22303661_IHL-FAQ.pdf.
International Court of Justice (ICJ) (2015) “Basic Documents: Statue of the Court,” retrieved from http://www.icj-cij.org/documents/?p1=4&p2=2.
Jung, Y. (2010) “Recurrence of DDoS Attacks against the Blue House, the Ministry of Foreign Affairs, and Naver.com,” retrieved from newshankuk.com/news/www.newshankuk.com/news content.asp? news_idx=20100708092500n5131 (in Korean).
Kim, H. (2010) “North Korea’s Cyber Terror and Information Warfare Capabilities, and Cyber Security Countermeasure Proposals,” retrieved from www.boan.com/news/ articleView.html?idxno=1391 (in Korean).
Kim, Y. (2015) “KHNP Hacking is Attributed to North Korea,” retrieved from www.pressian.com/news/ article.html?no=124755 (in Korean).
Kshetri, N. (2014) “Cyberwarfare in the Korean Peninsula: Asymmetries and Strategic Responses,” East Asia, Vol. 31, pp. 183–201.
Lee, M. (2011) “North Korean OS ‘Red Star 2.0’ Very Vulnerable against Cyberattacks,” Digital Daily, retrieved from www.ddaily.co.kr/news/article.html?no=84158 (in Korean).
Lee, S. (2009). National important information was leaked through a hole of the military Internet. Yonhap News. Retrieved from news.naver.com/main/ read.nhn?mode=LSD&mid=sec&sid1=100 &oid=001 &aid=0002922925 (in Korean).
Lee, Y., Kwon, H., Lee, J., and Shin, D. (2015) “Development of Countermeasures against North Korean Cyberterrorism through Research Case Studies,” The Korean Journal of Defense Analysis, Vol. 27, No. 1, pp. 71–86 (in Korean).
Libicki, M. (2013) “Brandishing Cyberattack Capabilities,” retrieved from www.rand.org/content/dam/rand/pubs/research_reports/RR100/RR175/RAND_RR175.pdf.
Lim, J., Kwan, Y., Chang, K., and Baek, S. (2013) “North Korea’s Cyber War Capability and South Korea’s National Counterstrategy,” The Quarterly Journal of Defense Study Policy Studies, Vol. 29, No. 4, pp 9–45 (in Korean).
Mansourov, A. (2014) North Korea’s Cyberwarfare and Challenges for the U.S.-ROK Alliance, Korea Economic Institute of America Academic Paper Series 2014, Korea Economic Institute of America, Washington, DC, US, pp. 1–17.
Ministry of Science, ICT, and Future Planning (MSIP), and Korea Internet and Security Agency (KISA) (2014) Korea Internet White Paper 2014, GPRN 11-B551505-000008-10, Myeong-jin C&P, Seoul, South Korea.
Park, D. (2011) “Study of Hacking in Terms of National Cyber Security Policy,” Review of the Korea Institute of Information Security and Cryptology, Vol. 21, No. 6, pp. 24–41 (in Korean).
Park, J. (2015) Finding Effective Responses against Cyber Attacks for Divided Nations, M.S. thesis, U.S. Naval Postgraduate School, Monterey, CA, US, December.
Park, Y. (2013) “Police Announced that Hacking on Joongang Ilbo in 2012 Was from North Korea,” Yonhap News, retrieved from www.yonhapnews.co.kr/society/2013/01/16/0701000000AKR2013011 6090400004.HTML (in Korean).
Pidathala, V., Khalid, Y., Singh, A., and Vashisht, S. (2013, March 21) “More Insights on the Recent Korean Cyberattacks (Trojan.Hastati),” retrieved from www.fireeye.com/blog/technical/ botnet-activities-research/2013/03/more-insights-on-the-recent-korean-cyber-attacks-trojan-hastati.html
Radunovic, V. (2013) “DDoS – Available Weapon of Mass Disruption,” Proceedings of the 2013 21st Telecommunications Forum (TELFOR), Geneva, Switzerland.
Richwine, L. (2014) “Cyberattack Could Cost Sony Studio As Much As 100 Million,” retrieved from www.reuters.com/article/2014/12/09/us-sony-cybersecurity-costs-idUSKBN0JN2L020141209.
Rowe, N. (2010) “Towards Reversible Cyberattacks,” Proceedings of the 9th European Conference on Information Warfare and Security, Thessalonika, Greece.
Rowe, N. (2015) “Distinctive Ethical Challenges of Cyberweapons,” in Tsagourias, N., and Buchan, R., (eds.), Research Handbook on Cyber Space and International Law, Edward Elgar, Cheltenham, UK, pp. 307-325.
Rowe, N. (2015) “Attribution of Cyberwarfare,” Chapter 3 in Green, J. (ed.), Cyber Warfare: A Multidisciplinary Analysis, Routledge, Oxon, UK, pp. 61-72.
Seo, S., Won, Y., and Hong, J. (2011, October) “Witnessing Distributed Denial-of-Service Traffic from an Attacker's Network,” 7th International Conference on Network and Service Management (CNSM), Paris, France.
Sherstobitoff, R. and Liba, I. (2013) “Dissecting Operation Troy: Cyberespionage in South Korea,” McAfee Labs White Paper, retrieved from http://www.mcafee.com/us/resources/white-papers/wp-dissecting-operation-troy.pdf.
Singer, P., and Friedman, A. (2014) Cybersecurity and Cyberwar: What Everyone Needs to Know (1st ed.), Oxford University Press, New York, NY.
U.S. CERT (2013, April 2) “South Korean Malware Attack,” retrieved from www.us-cert.gov/sites/ default/files/publications/South%20Korean%20Malware%20Attack_1.pdf.
Ventre, D. (2011) Cyberwar and Information Warfare, John Wiley and Sons, Hoboken, NJ, US.
Worden, R. (2008) North Korea: A country study, Library of Congress, Federal Research Division, retrieved from lcweb2.loc.gov/frd/cs/pdf/CS_North-Korea.pdf.