|
|
Precision
|
Recall
|
f-score
|
|
Threshold
|
|
|
|
|
0.1
|
0.1148
|
0.3521
|
0.1732
|
|
|
|
|
|
|
0.5
|
0.2061
|
0.2416
|
0.2224
|
|
|
|
|
|
|
1
|
0.5625
|
0.18
|
0.2727
|
|
|
|
|
|
|
1.5
|
0.4375
|
0.14
|
0.2121
|
|
|
|
|
|
|
2
|
0.4375
|
0.14
|
0.2121
|
|
|
|
|
|
|
5
|
0.375
|
0.12
|
0.1818
|
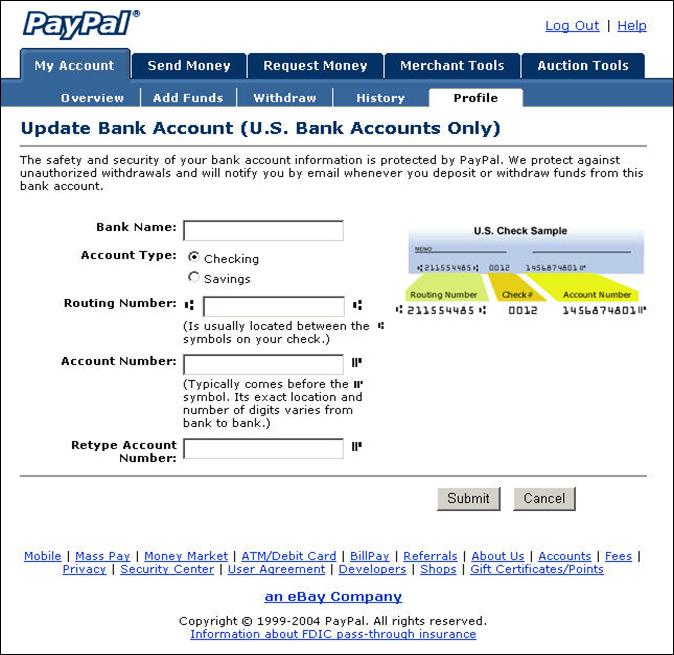
Table
7.
Precision and Recall with given odds threshold for double word clues to
identify phishing in our test set.
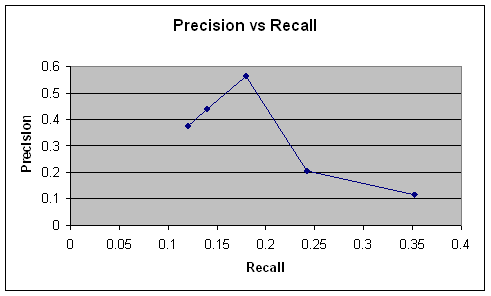
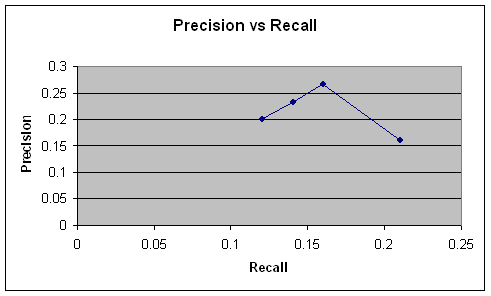
Figure
13. Precision
vs. Recall for bigram clues
THIS PAGE
INTENTIONALLY LEFT BLANK
Based on our analysis and experiments, we provide here
suggestions for countermeasures to prevent phishing attacks. The
countermeasures are organized by whom or what should be responsible for
implementing the countermeasure. Financial institutions and e-commerce
organizations should implement the following countermeasures.
·
Personalize all greetings in email correspondence. Phishing
emails are typically addressed as "Dear Customer" and not individually. Except
for instances of spear phishing, a personalized greeting would indicate that
the email is not a bulk phishing email and is most likely legitimate.
·
Ensure online correspondence with customers does not look
suspicious or provide material for phishers to take advantage of for future
scams. Avoid using inflammatory language and urgently requesting sensitive
information in an email. Email containing language that uses fear or
excitement and which attempts to rouse a sense of urgency should alarm the
recipient. Rather, inform the Internet user that they have a message in their
account inbox and direct them to log on the company Web site to retrieve the
message. All requests for information and submission of information should occur
on the company's secure Web site.
·
Never direct customers to submit sensitive information via a Web
form in an email. Web forms in email are a common phishing practice.
Companies should have users log on to a secure Web site to submit all requested
information.
·
Maintain valid security certificates from reputable well-known
third parties.
·
Monitor or pay for services that monitor domain-name registries
to prevent phishers from establishing fraudulent Web sites with similar domain
names, such as www.bankofthevvest.com.
·
Avoid providing hyperlinks in email correspondence to customers.
Eliminating hyperlinks in email does inconvenience users and businesses;
however, users will be assured of the legitimacy of the email.
As an example, Wells Fargo Bank
uses smart, safe, and authentic looking email correspondence as in Figure 12.
The only aspect of the email that could be criticized is the greeting. The
greeting should be personalized, but the email provides no reason to suspect
fraud and no means for a phisher to capitalize on the method of
correspondence. There are no clickable links, no inflammatory language, no
HTML, and the email does not request any sensitive information.
From: Wells Fargo Online
<ofsrep.alert_osn@wellsfargo.com
>
Date: Jun 3, 2006 11:52 PM
Subject: Wells Fargo Online statement notification
To: Todd.Smith@gmail.com
Dear Customer:
The statement for your account 711-5321XXX is now
available to view
online. To access your statement, please sign on to Wells Fargo
Online and
select the "View Online Statements" link on the Account History
screen.
Sincerely,
Wells Fargo,
Online Customer Service
Figure
14. Example
of proper email correspondence (Wells Fargo Bank)
Financial
institutions and e-commerce organizations should be responsible for providing
training to their users on their standard online business practices as well as
countermeasures for users to implement. Internet users should be responsible
for implementation of the following countermeasures.
·
Avoid using hyperlinks in emails regardless of the sender.
·
Log onto a Web site directly by typing the web address in the
browser address bar. Typing an address directly into the browser address bar
is a trustworthy method except in rare instances of pharming or DNS cache
poisoning which will be discussed later.
·
Avoid disclosing any sensitive information when requested in an
email and never submit sensitive information via HTML forms in email. Phishing
emails typically request personal sensitive information such as usernames,
passwords, social security numbers, credit card numbers, and mother's maiden
name.
·
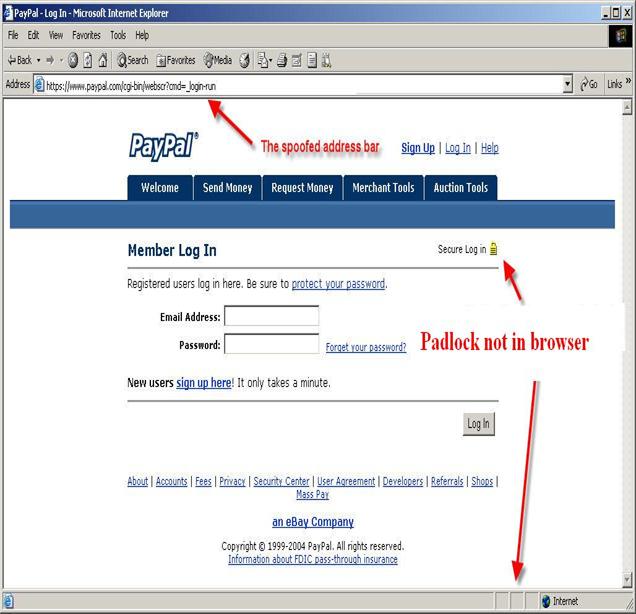
Check Web site security, ensure that the Secure Hypertext
Transfer Protocol (https) is employed in the browser address bar and the
padlock icon is shown in the bottom right portion of the browser chrome.
Verify security certificates are valid and from a trusted third party.
·
Ensure web browser is patched with all security related patches.
For Internet Explorer users, Microsoft has a patch for vulnerabilities that
certain phishing scams utilize http://www.microsoft.com/security/.
Automated
countermeasures may provide a viable defense as well.
·
Countering fake hyperlinks: Integrate a tool into web browsers
that compares the hyperlink text to the actual hyperlink when the user mouses
over the link browser, and disable any links that do not match. Our background
research as well as our own research shows that a displayed warning is
typically ignored or explained away, so automatically disabling the link is
most effective.
·
Spoofed address bar: Integrate a tool into web browsers that compares
the spoofed address to the actual address and have the browser close the Web
page and display an explanatory message if the addresses do not match.
Usability is always a concern, but where phishing is concerned, automated
programs must be forceful and not allow users to easily ignore security
warnings.
·
Disguised or undisguised fraudulent hyperlinks: Disable all
hyperlinks in an email.
·
Spoofed email header information: Before email is delivered to
an inbox, look at the full header information to analyze the route an email
message took to arrive. If the "from" and "by" fields of the received header
are inconsistent, that is indicative of a forged email header. Also, look for
inconsistency between the sender address domain and the site domain. This is a
good measure of legitimacy except for companies using a third party for online
correspondence and transactions like the PNC Bank example.
·
Use a hash table to compare Web site data to detect similar
appearing Web sites, which may be phishing.
·
Offensive countermeasure: Enter false information on the Web
site forms. If companies are receiving charge attempts or transactions with
bad credentials, this would indicate that phishers are trying to defraud users
and the company. If large numbers of forms are submitted with obviously false
information, this provides a kind of "denial of service" attack on
the phishing site as well as making it much easier for victimized credit-card
companies and other businesses to detect phishing on their accounts and respond
quickly. However, some phishing Web sites have started checking the validity
of credit card numbers with a publicly available formula that does not require
a connection to a credit-card server.
·
Both the unigram and bigram word clues provided useful
probabilities for classifying phishing email. The unigram and bigram word clues
may be used to filter phishing email or may be used in conjunction with other
defensive indications to positively identify a phishing attack. An effective means of using word clues would be to
flag an email as suspicious and combine the suspicious classification with
other defensive clues to accurately determine legitimacy. The automated tool
would have a pre-defined threshold probability for phishing. The tool would look
for clues like generic greetings, fake hyperlinks, and word clues. Each clue
would have an associated probability and if the combined probabilities reach
the pre-defined threshold, then the tool would alert the user that the email
and Web site are fraudulent.
·
Pharming: The only current defense against pharming is the
nslookup tool which looks up data on a given site. Designing an automated tool
that performs "nslookup" and warns the user from visiting fraudulent Web sites
may be a viable defense.
Our survey involving detection of fraudulent email/Web
site pairs provided useful information, but more people should be surveyed.
The survey could be converted to a Web format to allow a greater number and
range of participants and more data. Also, continually updating the examples
used in the survey with new forms of attack would provide fresh data and new
defense ideas.
Our second experiment involving conditional probabilities
of single word and double word clues in phishing email suggested there is a
good possibility that phishing emails can be detected with word clues, but it
is harder than detecting spam in general. This experiment could be enhanced by
using a broader and larger experimental set of email. The unigrams and bigrams
can be used to develop an automated filter to prevent attacks.
An important area our research did not focus on is
pharming, for which many of the countermeasures discussed in this thesis may be
appropriate. Pharming is a new phishing tactic that could allow phishers to
operate undetected. Pharming involves a fraudulent Web site used to collected
sensitive information from Internet users. It aims to redirect traffic from
legitimate Web sites to fraudulent Web sites while the client believes to be in
a trusted domain. Pharming is achieved in one of two ways. First, the
attacker can exploit a vulnerable DNS server; the server is "poisoned" by
changing the IP address of the target Web site to the IP address of the
fraudulent Web site. Internet users can enter the correct legitimate Web site
address in the address bar, but be directed to the fraudulent site, while the
address bar still displays the legitimate Web site address. Second, the
attacker can use malware to corrupt a client's host file which contains its own
local name to IP address mapping. There is currently no practical defense
mechanism for pharming.
The following survey involves ten emails and the
associated websites the emails direct the recipient to visit. The survey asks
for you to determine if the email/website pair appears to be fraudulent and
indicate which factors led you to believe it to be fraudulent. Before you look
at the first sample please answer the questions below.
1. Do you view website security certificates when
prompted?
Yes No
2. Have you ever used any tool to determine who owns an
IP address?
Yes No
3. Do you open emails in which you do not recognize the
sender?
Yes No
4. Do you view the full header information of an email?
Yes No
5. Do you use clickable links in emails?
Yes No
1. Please indicate
whether the email/website pair appears to have fraudulent intent or not.
Fraudulent Not
Fraudulent
2. If fraudulent, then on
a scale of 1-5, which factors lead you to believe the pair to be fraudulent? (Scale:
1-Not at all, 5-Key identifying factor)
Text of email:
1 2
3 4 5
Website address (e.g. www.nps.edu):
1 2 3 4 5
What the website looks
like:
1 2 3 4 5
Where the email came
from:
1 2 3 4 5
Clickable link in email:
1 2 3 4 5
Believability of claims
in email:
1 2 3 4 5
Please circle any other
factors here you use to determine an email/Web site is fraudulent.
-Spelling/Grammar -Webpage
Source code -Other:________
-Consistency -Security
features
-Unusual
Pronunciation -Specificity
|
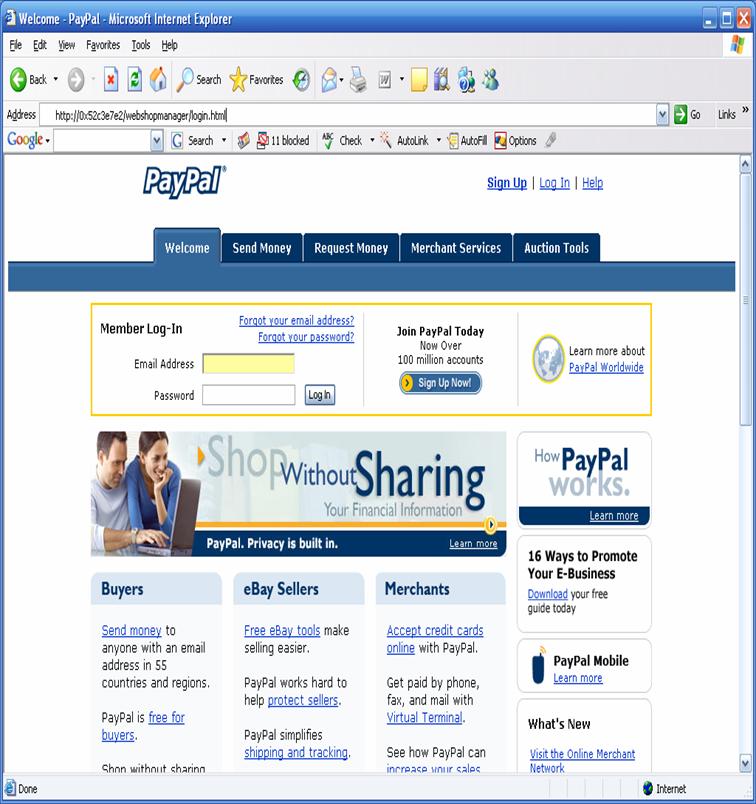
From:
|
"PayPal"
<admin@paypal.com>
|
|
Subject:
|
Notification of Limited Account Access
|
|
Date:
|
Sun, 5 Mar 2006 15:19:01 +0200
|
|

|
|

|
|
We recently reviewed your account, and we
need more information about your business to allow us to provide
uninterrupted service. Until we can collect this information, your access to
sensitive account features will be limited. We would like to restore your
access as soon as possible. We apologize for the inconvenience.
Why is my account
access limited?
Your account access has been limited for the following reason(s):
We have reason to believe that your account was accessed by a third party.
Because protecting the security of your account is our primary concern, we
have limited access to sensitive PayPal account features. We understand that
this may be an inconvenience but please understand that this temporary
limitation is for your protection.
(Your case ID for this reason is PP-136-124-102.)
How can I restore my
account access?
Completing
all of the checklist items will automatically restore your account access.
|
Copyright © 1999-2006 PayPal. All rights
reserved.
|
|
1. Please indicate
whether the email/website pair appears to have fraudulent intent or not.
Fraudulent Not
Fraudulent
2. If fraudulent, then on
a scale of 1-5, which factors lead you to believe the pair to be fraudulent? (Scale:
1-Not at all, 5-Key identifying factor)
Text of email:
1 2
3 4 5
Website address (e.g. www.nps.edu):
1 2 3 4 5
What the website looks
like:
1 2 3 4 5
Where the email came
from:
1 2 3 4 5
Clickable link in email:
1 2 3 4 5
Believability of claims
in email:
1 2 3 4 5
Please circle any other
factors here you use to determine an email/Web site is fraudulent.
-Spelling/Grammar -Webpage
Source code -Other:________
-Consistency -Security
features
-Unusual
Pronunciation -Specificity
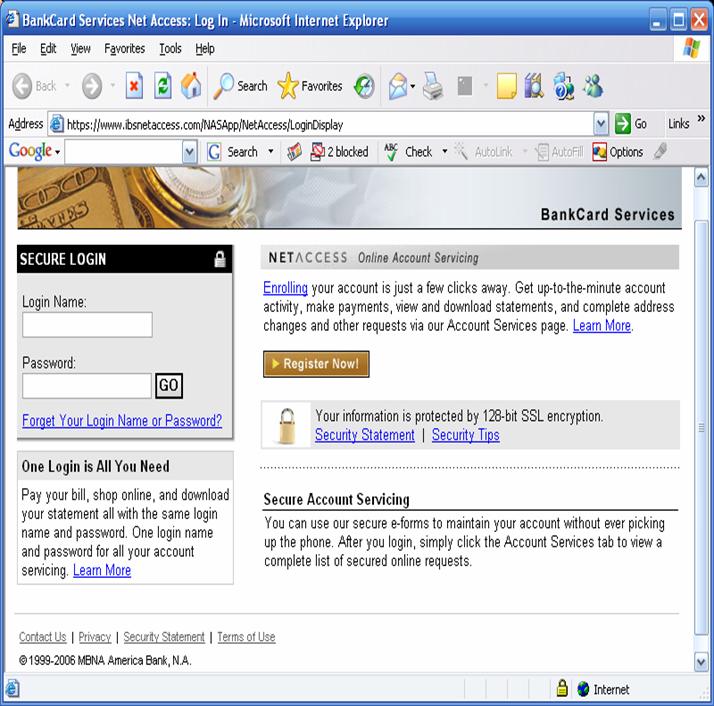
From: Individualized BankCard Services <mailto:IBS@email.cardsatisfaction.net>
Date: Apr 28, 2006 4:46 PM
Subject: Use your PNC Bank credit card today.
To: jackmcdowell@comcast.net
|

|
RE: Your account number ending in 3272
|
|

|
|
|
|
Dear Jack D. McDowell,
Enjoy the power of extra cash
this spring with a balance transfer. With a click, you can transfer
higher-rate balances to your PNC Bank Visa® credit card account. With
just one monthly payment, it's the perfect opportunity to:
- Get rid of
those department store balances.
- Make
improvements to your home for spring.
- Plan a summer
get-away.
- Join
a gym.
Why not? Just click to open up a world
of new possibilities for yourself. Go to http://links.cardsatisfaction.net/ajtk/servlet/JJ?H=25bwbv&R=1571356816&P=www.pncnetaccess.com to transfer balances, or visit
your local bank to get a cash advance.
|
|
|
Your
credit line is
$27,500!
|
|

|
|
Consolidate balances.
Make just one monthly
payment.*
|
|

|
|
|
|
|
|
|
|
1. Please indicate
whether the email/website pair appears to have fraudulent intent or not.
Fraudulent Not
Fraudulent
2. If fraudulent, then on
a scale of 1-5, which factors lead you to believe the pair to be fraudulent? (Scale:
1-Not at all, 5-Key identifying factor)
Text of email:
1 2
3 4 5
Website address (e.g. www.nps.edu):
1 2 3 4 5
What the website looks
like:
1 2 3 4 5
Where the email came
from:
1 2 3 4 5
Clickable link in email:
1 2 3 4 5
Believability of claims
in email:
1 2 3 4 5
Please circle any other
factors here you use to determine an email/Web site is fraudulent.
-Spelling/Grammar -Webpage
Source code -Other:________
-Consistency -Security
features
-Unusual
Pronunciation -Specificity
|
Date:
|
21 Mar 2006 02:52:13 -0800
|
|
To:
|
"John Crawford"
<JohnnyC@yahoo.com>
|
|
From:
|
"Amazon Marketplace"
<marketplace-messages@amazon.com>
|
|
Subject:
|
Rate Your Transaction
(058-2178846-0981142) at Amazon.com
|
|
Dear John Crawford,
Congratulations on your
purchase from textbookexec2 on 02/18/2006 05:40 PM PST.
|
|
Leave
Feedback About This Transaction
Please
take a moment to rate this transaction (058-2178846-0981142). It's
easy--just pick a rating and add any helpful comments. Your input will
help Amazon.com and our sellers continually improve the customer
experience. Your rating will apply to the following item:
·
1 of Phishing Exposed by Lance James [Paperback]
 (Need
Help?) (Need
Help?)
Need help?
If you have trouble with the "Leave feedback" button above,
you can rate your transaction by completing the following steps:
- Go to http://www.amazon.com/feedback.
- You'll
be prompted for a log-in.
- After
logging in, you'll see a list of all of the orders that need
feedback.
- Find
the order on the list and click the "Leave seller
feedback" button on the right.
If you have questions
regarding your transaction, we advise you to check with your seller
directly at textbookexec@hotmail.com
for details. To review your latest transactions, view Your Account.
|
|
|
|
|
Please note that
this message was sent to the following e-mail address: JohnnyC@yahoo.com
Copyright 2005
Amazon.com, Inc. All rights reserved.
|
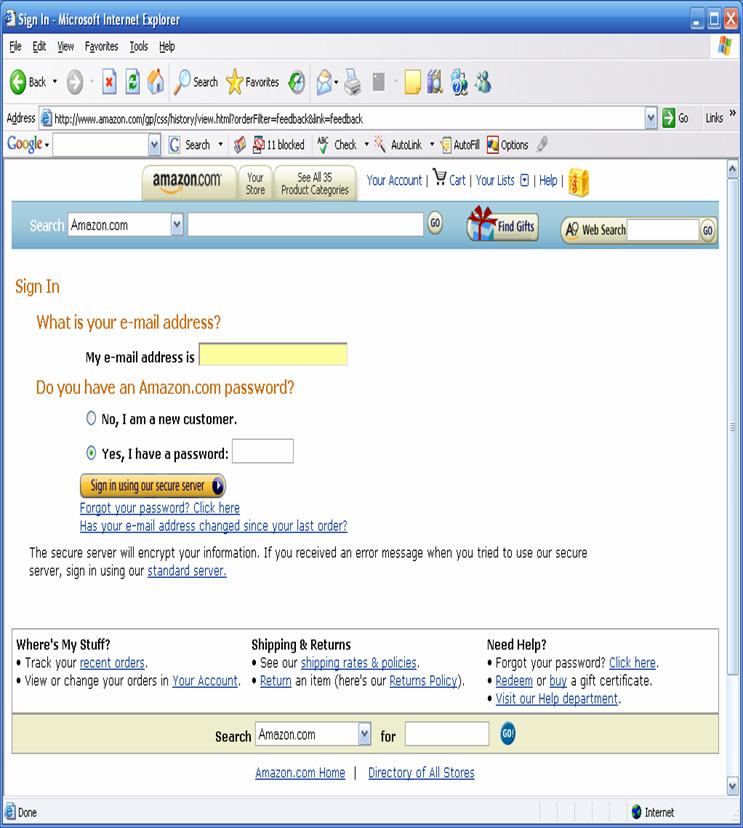
1. Please indicate
whether the email/website pair appears to have fraudulent intent or not.
Fraudulent Not
Fraudulent
2. If fraudulent, then on
a scale of 1-5, which factors lead you to believe the pair to be fraudulent? (Scale:
1-Not at all, 5-Key identifying factor)
Text of email:
1 2
3 4 5
Website address (e.g. www.nps.edu):
1 2 3 4 5
What the website looks
like:
1 2 3 4 5
Where the email came
from:
1 2 3 4 5
Clickable link in email:
1 2 3 4 5
Believability of claims
in email:
1 2 3 4 5
Please circle any other
factors here you use to determine an email/Web site is fraudulent.
-Spelling/Grammar -Webpage
Source code -Other:________
-Consistency -Security
features
-Unusual
Pronunciation -Specificity
|
Date:
|
Tue, 4 Apr 2006
14:09:51 +0200
|
|
To:
|
ds_barnes@yahoo.com
|
|
From:
|
customercare@chase.com
|
|
Subject:
|
NOTICE FROM CHASE
BANK
|
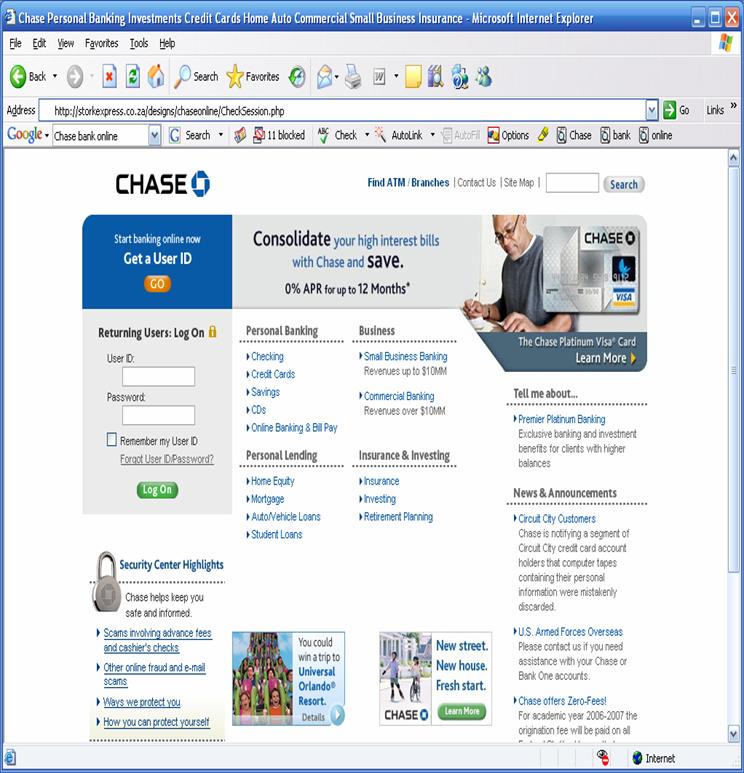
Dear Chase Bank Client,
This is your official notification from Chase Bank that the
service(s) listed below
will be deactivated and deleted if not renewed immediately. Previous
notifications have
been sent to the Billing Contact assigned to this account. As the Primary
Contact, you
must renew the service(s) listed below or it will be deactivated and
deleted.
Renew Now
your Chase Bank Bill Pay and Services.
If you are not enrolled in Online Banking, please enter your checking account
number as
Sign-in Username and Social Security Number as Password.
SERVICE : Chase Bank Bill Payment.
EXPIRATION: April 9, 2006
Thank you, sincerely,
Lionel Wood
Customer Service
========================================
IMPORTANT CUSTOMER SUPPORT INFORMATION
========================================
Document Reference:
(88856431).
2006 Chase Bank
4832
examples, 372542 nonexamples, 0.012804273744349108 probability.
Negative
Clues:
5.324813631522897E-4
0 938 computer
5.701254275940707E-4
0 876 program
5.720823798627002E-4
0 873 cellpad
5.733944954128441E-4
0 871 school
5.74052812858783E-4
0 870 cellspac
5.88235294117647E-4
0 849 faculty
6.527415143603133E-4
0 765 verdana
6.666666666666666E-4
0 749 paper
6.711409395973154E-4
0 744 bgcolor
6.729475100942127E-4
0 742 network
7.173601147776184E-4
0 696 include
7.621951219512195E-4
0 655 question
7.645259938837921E-4
0 653 technology
7.680491551459293E-4
0 650 science
7.763975155279503E-4
0 643 develop
7.937767899666614E-5
0 6298 font
8.237232289950577E-4
0 606 naval
8.403361344537816E-4
0 594 netflix
8.547008547008547E-4
0 584 head
8.771929824561404E-4
0 569 week
8.787346221441124E-4
0 568 project
8.849557522123894E-4
0 564 left
9.433962264150943E-4
0 529 postgraduate
9.671179883945841E-4
0 516 title
0.001004016064257028
0 497 data
0.0010183299389002036
0 490 conference
0.0010204081632653062
0 489 submit
0.0010330578512396695
0 483 discuss
0.0010504201680672268
0 475 university
0.0010548523206751054
0 473 space
0.0010615711252653928
0 470 3dmsonorm
0.0011037527593818985
0 452 fund
0.0011135857461024498
0 448 issue
0.0011135857461024498
0 448 plan
0.0011394712853236098
2 2191 color
0.0011467889908256881
0 435 current
0.0011574074074074073
0 431 write
0.0011655011655011655
0 428 topic
0.0011682242990654205
0 427 internets
0.001182033096926714
0 422 nextpart
0.0012254901960784314
0 407 engineer
0.0012285012285012285
0 406 security
0.0012345679012345679
0 404 thesis
0.0012355848434925864
1 1212 strong
0.0012376237623762376
0 403 new
0.0012468827930174563
0 400 request
0.0012594458438287153
0 396 search
0.0012594458438287153
0 396 webpronew
0.001272264631043257
0 392 describe
0.001272264631043257
0 392 harvard
0.0012755102040816326
0 391 view
0.001282051282051282
0 389 colspan
0.001288659793814433
0 387 require
0.0012919896640826874
0 386 11px
0.0012919896640826874
0 386 delivery
0.0012953367875647669
0 385 gmail
0.0013020833333333333
0 383 background
0.0013089005235602095
0 381 professor
0.0013157894736842105
0 379 test
0.0013192612137203166
0 378 message-id
0.0013192612137203166
0 378 teach
0.0013477088948787063
0 370 account
0.0013736263736263737
0 363 body
0.0014005602240896359
0 356 esmtp
0.0014124293785310734
0 353 charset
0.0014124293785310734
0 353 update
0.0014367816091954023
0 347 shape
0.0014534883720930232
0 343 smtpsvc
0.001483679525222552
0 336 alumni
0.0015015015015015015
0 332 bfi0
0.0015151515151515152
0 329 newsletter
0.0015290519877675841
0 326 design
0.0015479876160990713
0 322 sensor
0.001567398119122257
0 318 model
0.001597444089456869
0 312 rect
0.001607717041800643
0 310 committee
0.0016181229773462784
0 308 cs-announc
0.001639344262295082
0 304 format
0.0016835016835016834
0 296 academic
0.0016891891891891893
0 295 10px
0.0016891891891891893
0 295 return-path
0.0017064846416382253
0 292 |hour 9
0.001718213058419244
0 290 |hour 1
0.001736111111111111
0 287 author
0.001736111111111111
0 287 copy
0.0017421602787456446
0 286 10pt
0.0017482517482517483
0 285 print
0.0017543859649122807
0 284 3dhttp
0.0017605633802816902
0 283 product
0.0017667844522968198
0 282 0pt
0.0017667844522968198
0 282 coord
0.0017730496453900709
0 281 |hour 2
0.0017793594306049821
0 280 quoted-print
0.0017921146953405018
0 278 line-height
0.0017985611510791368
0 277 redshift
0.0018050541516245488
0 276 found
0.0018050541516245488
0 276 iso-8859-1
0.0018050541516245488
0 276 result
0.0018115942028985507
0 275 a676
0.0018181818181818182
0 274 media
0.0018315018315018315
0 272 content-class
0.0018315018315018315
0 272 horn
0.0018315018315018315
0 272 suggest
0.0018450184501845018
0 270 bold
0.0018656716417910447
0 267 tigerdirect
0.0018796992481203006
0 265 hear
0.0018796992481203006
0 265 opportune
0.0018867924528301887
0 264 en-u
0.001893939393939394
0 263 base
0.0019011406844106464
0 262 document
0.0019011406844106464
0 262 epson
0.0019083969465648854
0 261 game
0.0019083969465648854
0 261 localhost
0.0019157088122605363
0 260 language
0.0019157088122605363
0 260 public
0.0019230769230769232
0 259 communicate
0.0019455252918287938
0 256 workshop
0.001953125
0 255 create
0.001953125
0 255 solve
0.001976284584980237
0 252 spawar
0.0020242914979757085
0 246 institute
0.0020325203252032522
0 245 educate
0.00205761316872428
0 242 future
0.00205761316872428
0 242 train
0.00205761316872428
0 242 |hour 4
0.002066115702479339
0 241 suntop
0.002074688796680498
0 240 college
0.0020833333333333333
0 239 akamaitech
0.0020833333333333333
0 239 firewall
0.0021008403361344537
0 237 technic
0.002109704641350211
0 236 redir
0.002109704641350211
0 236 tool
0.002127659574468085
0 234 schedule
0.002136752136752137
0 233 bottom
0.002136752136752137
0 233 origin
0.002145922746781116
0 232 compute
0.0021551724137931034
0 231 cost
0.0021551724137931034
0 231 final
0.0021551724137931034
0 231 purchase
0.002183406113537118
0 228 subscribe
0.0022026431718061676
0 226 award
0.0022026431718061676
0 226 commune
0.0022026431718061676
0 226 hour
0.0022123893805309734
0 225 feature
0.0022222222222222222
0 224 control
0.0022222222222222222
0 224 delivered-to
0.002242152466367713
0 222 do
0.002242152466367713
0 222 participate
0.0022727272727272726
0 219 ieee
0.0022727272727272726
0 219 sponsor
0.00228310502283105
0 218 chair
0.0022935779816513763
0 217 Prof
0.0022935779816513763
0 217 ientri
0.0022935779816513763
0 217 ientrymail
0.0022935779816513763
0 217 rowspan
0.0022935779816513763
0 217 source
0.002304147465437788
0 216 machine
0.0023148148148148147
0 215 navy
0.002325581395348837
0 214 defense
0.002347417840375587
0 212 digit
0.002347417840375587
0 212 value
0.0023584905660377358
0 211 window
0.002369668246445498
0 210 store
0.002369668246445498
0 210 try
0.002403846153846154
0 207 edit
0.002403846153846154
0 207 unsubscribe
0.002407704654895666
1 621 applicate
Positive
Clues:
0.19293478260869565
35 148 limit
0.19879518072289157
16 66 protect
0.203125 6
25 anymore
0.203125 6
25 sensitive
0.2073170731707317
8 32 delay
0.2080745341614907
33 127 notify
0.20833333333333334
12 47 apology
0.21014492753623187
14 54 transact
0.22058823529411764
7 26 foreign
0.22727272727272727
22 76 immediate
0.2288135593220339
13 45 obtain
0.24008810572687225
54 172 yahoo
0.2403846153846154
12 39 claim
0.24152542372881355
28 89 money
0.2661290322580645
16 45 delete
0.2973568281938326
67 159 paypal
0.3046875
19 44 verify
0.37272727272727274
20 34 Card
0.5092592592592593
27 26 renew
0.7442748091603053
97 33 bank
0.8582474226804123
166 27 paypal
0.8854166666666666
42 5 chase
0.953125 30
1 mber
0.9848484848484849
32 0 riti
0.9848484848484849
32 0 thro
0.9901960784313726
50 0 bject
0.9971751412429378
176 0 acco
4784 examples,
372070 nonexamples, 0.012694571372467852 probability.
Strong
Negative Clues:
3.952569169960474E-4
0 1264 PM send
4.3975373790677223E-4
0 1136 font size
4.6816479400749064E-4
0 1067 AM send
9.671179883945841E-4
0 516 postgraduate school
9.98003992015968E-4
0 500 font color
0.0013157894736842105
0 379 computer science
0.0019305019305019305
0 258 face are
0.002008032128514056
0 248 area shape
0.002109704641350211
0 236 School naval
0.002136752136752137
0 233 rect coord
0.002173913043478261
0 229 g akamaitech
0.0022026431718061676
0 226 A href
0.0022727272727272726
0 219 style 3d'margin-left
0.002304147465437788
0 216 redir internets
0.002304147465437788
0 216 www netflix
0.0023584905660377358
0 211 span class
0.0024154589371980675
0 206 width 100%
Strong
Positive Clues:
0.4125 16
23 the service
0.5078125
32 31 to address
0.515625 16
15 and delete
0.6770833333333334
32 15 address book
0.9285714285714286
32 2 mobile alert
0.9517543859649122
108 5 can call
0.9517543859649122
108 5 go ahead
0.9517543859649122
108 5 help link
0.9539473684210527
72 3 email notify
0.9539473684210527
72 3 of limit
0.9539473684210527
72 3 the offer
0.955026455026455
180 8 the primary
0.9587765957446809
360 15 and delete
0.9601769911504425
108 4 help center
0.9601769911504425
108 4 this form
0.9601769911504425
108 4 to release
0.9666666666666667
72 2 limit access
0.9666666666666667
72 2 of charge
0.9666666666666667
72 2 please verify
0.9674329501915708
252 8 please confirm
0.9848484848484849
32 0 Add mobile
0.9848484848484849
32 0 paypal acco
0.9852941176470589
33 0 chase bank
0.9901960784313726
50 0 S bject
0.9930555555555556
71 0 r acco
THIS PAGE INTENTIONALLY LEFT BLANK
1.
Anti-Phishing Working Group(APWG), Committed to Wiping Out Internet Scams
and Fraud. Retrieved May 10, 2006 from http://www.antiphishing.org/index.html
2.
Dhamija, R., Tygar, J., &
Hearst, M. (2006). Proceedings of the Conference on Computers and Human
Interaction: Why Phishing Works. Montréal, QB, Canada.
3.
Government Accounting Office. (2005).
Information Security: Emerging Cybersecurity Issues Threaten Federal Information
Systems. Retrieved December 1, 2005 from
www.gao.gov/cgi-bin/getrpt?GAO-05-231
4.
Fogg, B.J. (2003). Persuasive Technology: Using Computers to Change
What We Think and Do. San Francisco: Morgan Kaufmann Publishers.
5.
Jagatic, T., Johnson, N., Jakobsson, M., & Menczer F., (2005) Draft
Preprint for Communications of the ACM: Social Phishing. Retrieved
March 16, 2006 from http://www.indiana.edu/~phishing/social-network-experiment/phishing-preprint.pdf
6.
Jakobsson, M. & Ratkiewicz, J. (2006). Proceedings of the
Conference on the World Wide Web: Designing Ethical Phishing Experiments.
Edinburgh, Scotland.
7.
James, L. (2005). Phishing Exposed. Rockland, MA: Syngress
Publishing, Inc.
8.
Mailfrontier. Press Release: Phishing IQ Test. (March 30, 2005).
Retrieved Jan 10, 2006 from http://www.mailfrontier.com/press/press_uk_phishingtest.jsp
9.
MessageLabs Intelligence. (2005). Annual Security Report: Cyber-criminals
Narrow Their Focus. Retrieved January 26, 2006 from www.messagelabs.com/Threat_Watch/Intelligence_Reports.
10.
Ragucci, J.W. & Robila, S.A. (2006). Societal
Aspects of Phishing. Retrieved May 16, 2006 from http://pages.csam.montclair.edu/~robila/RSL/Papers/istas06_2.pdf
11.
Wu, M., Miller, R.C., & Garfinkel, S.L. (2006). Proceedings of the
Conference on Computers and Human Interaction: Do Security Toolbars
Actually Prevent Phishing Attacks? Montréal, QB, Canada.
THIS PAGE
INTENTIONALLY LEFT BLANK
1.
Defense Technical Information Center
Ft. Belvoir, Virginia
2.
Dudley Knox Library
Naval Postgraduate School
Monterey, California
3.
Craig Martell
Naval Postgraduate School
Monterey, California
4.
Neil Rowe
Naval Postgraduate School
Monterey, California
5.
David S. Barnes
Naval Postgraduate School
Monterey, California