Inexpensive Seismic Sensors for Early Warning of Military Sentries
Gurminder Singh, Capt. Peter J. Young, Neil C. Rowe, and Thomas S. Anderson[*]
U.S. Naval Postgraduate School, Monterey, CA
Abstract�
Small military units operate under stressful conditions with limited resources.� A lightweight mobile surveillance system could reduce the effort to conduct sentry duties, and could help prevent ambushes or other types of attacks.� We explore the use of built-in sensors and networking abilities of modern "smartphones" to fill this gap.� Current smartphones use accelerometers to sense changes in orientation of the phone.� This same capability can be used to detect vibrations in the ground produced by approaching footsteps or vehicles.� We discuss the sensitivity of the phone, the filtering techniques, and the footstep signatures registered by the phone.� We then discuss the possible deployment configurations of single and multiple sensors to create a sensor grid that can be networked together.� Key concerns are ground noise, sensitivity of the phone, and distance between networked phones.�
This paper appeared in the Proceedings of SPIE Defense, Security, and Sensing Conference, Vol. 7693, Orlando, Florida, April 2010.� Keywords: sensor, smartphone, seismic, surveillance, footstep, detection, sentry, warning
1. INTRODUCTION
Small unit military operations are often fast-paced and resource-constrained, and can often end up in situations where the safety of the unit as a whole rests on the shoulders of a watchful team member.� Fatigue may inevitably degrade the team�s situational awareness.� In such situations, the team runs the risk of being ambushed by the enemy leading to loss of life and property.� Such situations are also common in distributed warfighting where small units conduct operations in remote, austere environments where security must be supplied by the unit itself.� The demand for technology-enhanced situational awareness is useful for both conventional and unconventional military activities.� In the civilian domain, similar requirements exist where people are stationed in remote areas and risk being attacked by animals and/or criminals.
We are studying a lightweight and low-power non-line-of-sight monitoring capability to alert about human, animal, and machinery movement nearby.� This situational awareness is implemented using existing equipment, without introducing significant additional weight to warfighter�s gear, using very little power, and is easy to install and operate.
We present several embodiments of a system that achieves this capability by using the latest commercial smartphones augmented with simple extensions.� This system is able to detect the presence of suspicious entities tens of meters away and immediately provides alerts to the tactical operator.� Our primary sensing mechanism in the system is seismic and is implemented using the accelerometers built into the smartphones.� We create a network of smart phones using Bluetooth to provide a robust surveillance capability.
There has been a growing trend for embedding a variety of sensors in smartphones.� The most common are GPS, accelerometer and photo sensors.� This trend is likely to continue with more low-power sensors being integrated.� Combined with their improved processing, storage and networking capability, this opens up possibilities for implementing innovative applications running on smart phones such as the one we have developed.�
The key research issues for our work are:
� Detecting low-strength signals at least 10 meters away by using sensors embedded in a smart phone.
� Developing techniques to minimize false negatives and false positives.
� Developing algorithms to minimize energy consumption on each node.
� Developing a energy-efficient virtual fence using multiple network nodes.
In our first implementation, we have focused on detecting human footsteps using an iPhone.� There are a number of other phones which come equipped with the sensors needed for our work, but we decided to use the iPhone as it is a popular and powerful phone sufficient for our application.� While we have not investigated in detail, we believe that the same capability can be implemented just as well or better on several other phones too.
In the rest of this paper, we describe our system and show our test results.� We describe in detail our filtering mechanism used to separate signal from the noise captured by the phone sensor.� While our research is still in early stages, we are encouraged to note that it is indeed possible to build a good seismic detector using COTS smart phones.�
2. The accelerometer and filtering
The Smartphones we used in our experiments were the Apple IPhone 3GS, jailbroken, featuring LIS302DL accelerometer1.� The LIS302DL has dynamically user selectable full scales of � 2g/� 8g and it is capable of measuring accelerations with an output data rate of 100 Hz or 400 Hz.2.� The accelerometer function in the IPhone produces three floating point values every time the didAccelerate method is accessed.� When setting the accelerometer access rate to .01, which means operating the accelerometer at 100 samples per second, we have noticed an average of 98 accesses per second.� This means we are dropping on average 2 hertz.� So the ability of the LIS302DL accelerometer to operate at 400 Hz does not translate to 400 accesses of the didAccelerate method apparently due to the calculations performed each time didAccelerate is called.�
The signals received from the accelerometer are expressed in three float values, one for each coordinate axis.� In our program, we store these values an NSMutableArray.� The first steps taken are done on the phone at the time the didAccelerate method fires.� We remove the baseline gravity force that is pulling on the accelerometer to leave instantaneous changes in movement.� This is done by a high-pass frequency filter that subtracts the low-pass values from each acceleration values.�� The code used to accomplish this is seen in example 1.�
|
#define kFilteringFactor 0.1 |
|
|
|
- (void)accelerometer:(UIAccelerometer *)accelerometer didAccelerate:(UIAcceleration *)acceleration { |
|
|
|
��� accelX = acceleration.x - ( (acceleration.x * kFilteringFactor) + (accelX * (1.0 - kFilteringFactor)) ); |
|
��� accelY = acceleration.y - ( (acceleration.y * kFilteringFactor) + (accelY * (1.0 - kFilteringFactor)) ); |
|
��� accelZ = acceleration.z - ( (acceleration.z * kFilteringFactor) + (accelZ * (1.0 - kFilteringFactor)) ); |
|
} |
Example 1, (IPhone OS Reference Library)
We explored several approaches to signal processing of the accelerometer data.� Since footsteps create waves in all three dimensions, it is useful to take the norm of the acceleration readings in all three axis for detection.� Experiments confirmed that this norm had increased signal to noise ratio as compared to measuring just the vertical acceleration when the phone was placed upright.� Since footstep seismic signals are predominantly low-frequency phenomenon between 10 and 100 hertz3, we sampled at 0.01 seconds.� To further reduce noise, we subtracted a threshold value equal to the mean value of the signal plus a constant (4.0 in most experiments) times the standard deviation.� All values less than zero were then set to zero.� This greatly enhanced footstep peaks, as shown in Figure 1.
For comparison, Figure 2 shows the results of similar processing on a conventional microphone during the same experiment (but not the same time period).�� It can be seen that the peaks are more blurred despite the fewer number of them due to their longer persistence.� Furthermore, the noise level was higher compared to the footsteps signals even with wind baffles on the microphones: We used the mean plus 2.0 times the standard deviation rather than 4.0 to get the same number of peaks.� This suggests that background noise is definitely a more serious problem with conventional microphones than with the vibration sensor, despite the presence of other causes of vibration such as a road nearby.� Figure 3 shows that analysis of the frequency domain is not much help for our phone vibration signal since it picks up a wide range of noise, unlike with more expensive seismic sensors carefully buried in the ground3.� Hence our thresholding of the magnitude of the raw signal is the only approach likely to work.� We are limited by the quality of our sensors, however, and sensors like geophones can provide considerably more accurate detection using more sophisticated mathematical methods4.
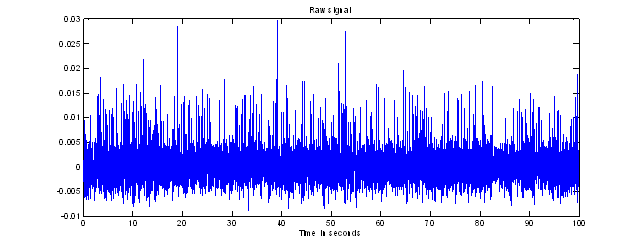
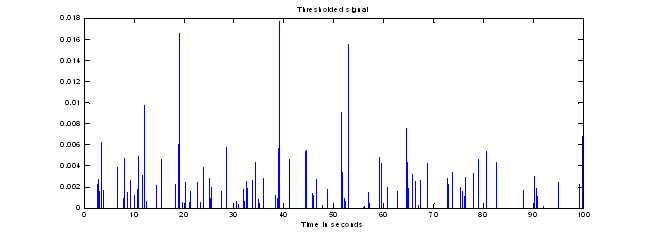
Figure 1: Example raw sensor norms over 100 seconds, and the results of processing and thresholding it.
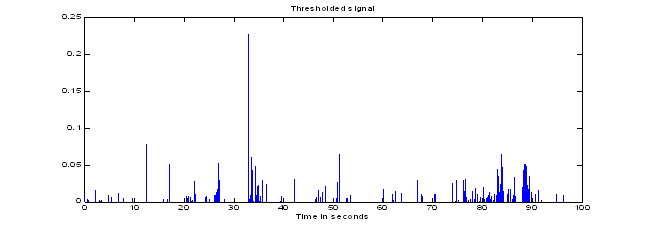
Figure 2: Similar analysis of peaks of an audio signal for comparison.
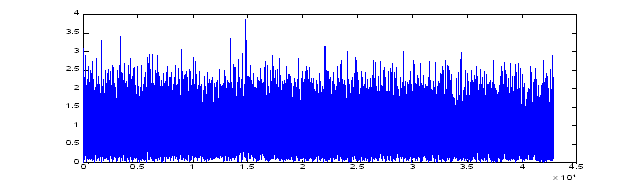
Figure 3: Norm of the Fourier spectrum for the Figure 1 signal.
3. Testing and results
Preliminary experiments were conducted at our school.� But we are also starting tests on packed dirt surfaces on a back road miles from any traffic, so that there is no possibility of contamination from outside sources.� We created a makeshift stand from parts bought from the local hardware store for less than four dollars.� The main component of the stand is some form of stake that is driven into the ground that will transfer ground vibrations to the phone.� Future tests will be conducted based on different lengths and type of material to determine the most effective combination.�
1. Clear ground of debris and dig slight depression of about two to four inches into ground. Geophones and devices like ours become more effective the closer the device is to surface level.�
2. Place phone in stand and begin application. Beginning the application, in our program, begins accessing the didAccelerate method at a rate of 100 times per second. While the program is running these values are stored in the NSMutableArray.
3. Start video camera to record actual personnel movement around the phone. The camera allows us to correlate the location of the individual walking to the anomalies found in the data.��
4. Tap phone 5 times to create a reference point in data to begin test.� This reference point is used when syncing the camera to the graphs.
5. Run test with periods of walking and periods of no movement. We found it important to give the phone periods of no movement; this allowed us to determine the base line noise of the accelerometer.�
6. Transfer data to a computer for filtering and analysis.� Currently this is done manually using the Jailbroken IPhone application called NetATalk, but will eventually be done with wireless communication.
4. footstep detectioN
Once the data is received and processed, we must determine when to raise an alarm.� To distinguish footsteps from other acoustic-impulse phenomena and the remaining background noise, we look for sequences of similar impulsive sounds that appear periodically at an interval of 0.47 to 0.63 seconds apart, consistent with the range of slow to fast cadences for walking adult males4.� The longer such a sequence we can find, the more confident we can be that its component sounds represent footsteps.� We found this method quite effective in detecting footsteps, more so than a single-footstep analysis method such as calculation of the second, third, and fourth moments and comparison of them to idealized footsteps.� It worked well for acoustic as opposed to seismic signals of footsteps5.� Footsteps also follow an inverse-square law with distance.� So with straight paths like those followed predominantly by our subjects, we should see a single large footstep peak at the time of the closest approach to the phone, preceded by a monotonic increase and followed by a monotonic decrease.� If we do not see this pattern, it is less likely to be a footstep sequence.
For Figure 1 for example, the strongest evidence (rated 8.4) found for footsteps was in the time period 7.0 to 12.7 where a sequence of five impulses matched well to a footstep sequence.� Also good were time periods 29.5 to 32.1 (rated 5.8), and 89.4 to 92.4 (rated 5.4). Further signal process techniques are being explored to improve the detection capability.
5. Small Unit deployment options
Phone sensors could be deployed in s a wide variety of configurations.� The goal is to maximize the effectiveness of each sensor.� Figure 4 shows several possibilities for uses at the fire-team and platoon level (4-15 people) that are based on defensive and offensive scenarios.� The calculations used are based on a six meter detection radius on each phone.� As our filtering of the Smartphones accelerometer data improves, this radius will increase.� However, our goal of using only phones and no other external wireless networking means that if we want to raise a silent alarm networked back to a base phone, our connections will be limited to the Bluetooth connectivity that we can achieve between phones.� A second concern is the battery life of phones.� It would not be practical to use all the phones in a small unit for the entire night with current Iphones, because this would drain the battery of the every phone in the unit over the course of one night.� This battery technology would need to be improved before phones could be deployed in a combat situation, either by increased battery life or interchangeable batteries.
Figure 4 shows a possible configuration of a four-man team.� Standard procedure is to keep five to twenty meters of dispersion between individual members of the fire team or platoon6,7.� �The fire team can be arranged in individual positions or �buddy� positions.� The main limitation is the number of phones.� If the team does not want to carry extra phones, they are reduced to one per team member, which would mean four phones for a fire team that they carry with them.� It will not be possible then for the unit to have 360-degree security without the coverage area encroaching on the sleeping area of the unit, thus causing false alarms.� The situation of the fire-team�s position can alleviate this as seen in the configuration on the right side.� But often a team is in a position where they have a friendly area on one side, and 180-degree security is sufficient (as on the right side of Figure 4).� They will be able to concentrate their sensors to cover an enemy approach from a particular direction.
�
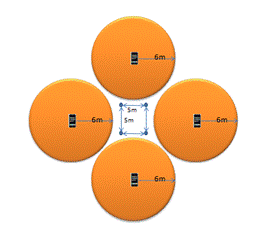
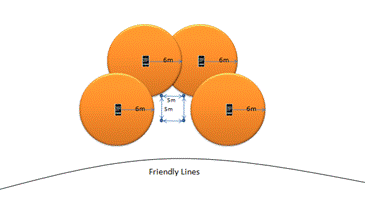
Figure 4: Situation 1: Fire-team night watch with maximum sensors.
���������������
These situations use all of the team�s phones as sensors.� The alarms produced in these situations could be an auditory or visual.� Visual alarms could avoid alerting the enemy that they have been detected, permitting more effective preparations for defense.� An enemy moving in would trip an alarm that would give the sentry time to wake his team and prepare to repel the assault.� We may only give the soldiers a few precious seconds of warning, but these seconds could mean the difference between being surprised and being prepared.� In the situations like the above, we could deploy three phones, and reserve the fourth for a base station silent alarm.� Figure 5 shows modified deployments for this case of three phones.

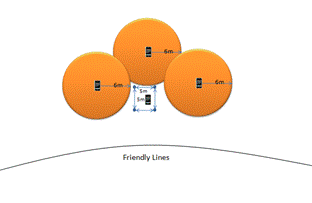
Figure 5: Situation 2: Fire-team night watch with silent alarm.
�����������������������
In Figure 6, the left side shows a possible use of sensors to extend the effectiveness of a platoon listening post.� When a platoon or company sets up a defensive position, the commander is tasked with recognizing likely avenues of approach and deploying listening/observation posts. (United States Marine Corps, 1978).� �These posts are tasked with providing an early warning of an imminent enemy assault.� The listening post is forward of the defensive position, and have radio or wire communication back to the defensive command post.� The listening post could extend their situational awareness even further by placing sensors further out.� In a platoon or company situation, more phones would be available giving the listening post the ability to have a base station in addition to any sensors they would emplace.� Depending on the terrain and range that could be achieved from the Bluetooth connectivity, we could network the sensor alarms back to the defensive command post as well.�
The right side of Figure 6, shows how sensors can be deployed in a defensive situation where certain avenues of approach are obscured by land features.� The sensors could be placed behind hills, trees, or buildings that an approaching enemy would use to mask their movement.� The sensor could also be placed directly in the likely avenue of approach.� If the approach were visible and well covered by heavy weapons, a tripped sensor could be a trigger line for the defense to open fire.� A sensor has a known range, and when it is tripped, the defensive line will have fairly accurate idea of the range of the enemy as long as the distance to the phone is known.�
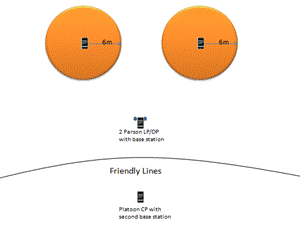
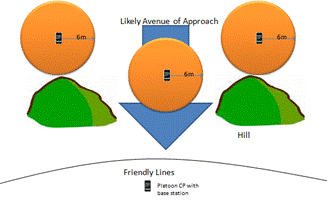
Figure 6: Situation 3: Platoon/company defensive positions.
The idea of using a phone as a trigger point could also be useful in an ambush situation. A concealed phone could be used when a unit is set up for an ambush, it would give the attacking unit a way to track the approaching unit as it heads to the ambush area. The ambush could be set to commence as when the phone alert, silent or auditory, is sounded.
6. Optimal deployment
When a deployment will persist for some time, it is
useful to develop methods for near-optimal deployment if possible.� A
reasonable simplification is to assume that each phone provides detection
within a fixed radius R.� Then if we have M phones, we can provide complete
coverage with a circle of phones at distance D if ![]() �or when
�or when ![]() .� For our experimental radius of
R=6 meters and six phones, this is 11 meters.� However, having a phone so close
is overly conservative and may not provide sufficient time for warfighters to
react.� If we deploy them in a wider radius, we can get a good chance of
detection while providing adequate warning.� If we deploy them in a circle at a
radius of
.� For our experimental radius of
R=6 meters and six phones, this is 11 meters.� However, having a phone so close
is overly conservative and may not provide sufficient time for warfighters to
react.� If we deploy them in a wider radius, we can get a good chance of
detection while providing adequate warning.� If we deploy them in a circle at a
radius of ![]() ,
we should get a probability of detection of an incursion of 1/K if incursions
occur in random directions of approach.� �A circle is the best deployment
pattern for optimal detection because a circle is the curve that covers the
maximum amount of area for the minimum amount of length of a closed curve.
,
we should get a probability of detection of an incursion of 1/K if incursions
occur in random directions of approach.� �A circle is the best deployment
pattern for optimal detection because a circle is the curve that covers the
maximum amount of area for the minimum amount of length of a closed curve.
Three general factors affect the value of deployment as a function of distance.� �As threats approach, they become more noticeable because their visual angle increases inversely with distance.� Similarly, the amount of visual angle from the sentry position that can be covered by a phone at a given distance decreases inversely with distance, so if threats are approaching from random directions, a threat twice as far will find it twice as easy to evade the same number of phones.� On the other hand, the value of coverage increases linearly with distance because, if the threat is approaching at a constant rate, the time to prepare for the threat increases with distance, and this is roughly linearly proportional to the distance.� So we have two factors that are inversely proportional and one that is proportional, for a net effect of inverse proportionality.� Thus it is generally desirable to put phones close by in the absence of other information about the direction of the threats.
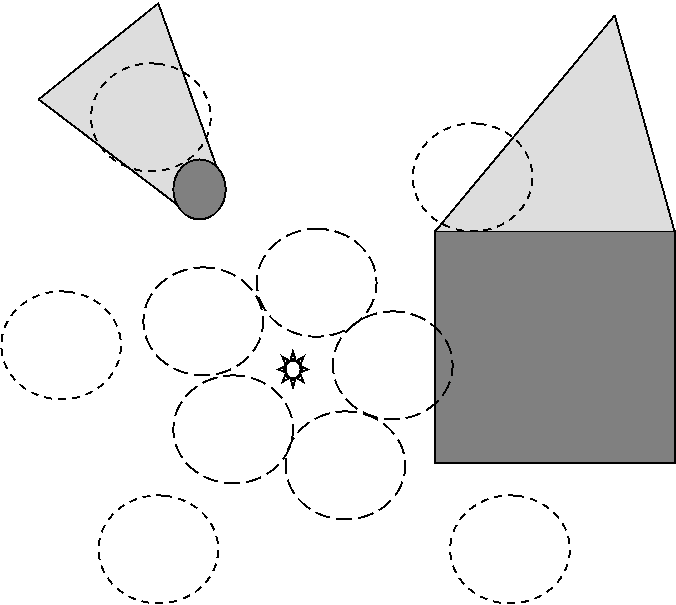
If incursions are not equally likely in all directions, we need to adjust the deployment scheme to handle this.� Of course, adversaries try to take advantage of the possibilities offered by terrain, and will prefer areas that provide good concealment.� One approach is to use a binary weighting scheme, where terrain that is not visible from a fixed sentry point is more important to monitor by a fixed ratio than terrain that is visible.� Such terrain can be found with a terrain map by sweeping a ray clockwise around the proposed sentry position to find obstacles.� When it encounters an obstacle, it traces the obstacle to the right until it reaches a discontinuity in depth, and then searches again to find the next obstacle if any.� This allows construction of a profile of the nearest obstacles to a point.� Then all terrain behind these obstacles represents hiding places of higher suitability for monitoring.� We can plan the emplacement of sensors on such terrain by a "greedy" algorithm which tries to successively situate phones at the locations that maximally reduce the probability of failing to detect an incursion in a range of bearing from the sentry point.� For instance, consider the terrain in Figure 7 with a building on the right (the solid square) and a tree on the left (the solid circle), and a sentry position on the bottom (the star).� We could use the inner dashed circles to get complete coverage at a short distance, or we could use the outer deployment of smaller-dashed circles to get coverage of 70% of the likely approaches, assuming that concealed areas (shaded) are four times as important to monitor as unconcealed ones.
7. Communications
We will use Bluetooth to communicate from the phones to a collection node, perhaps another phone.� Since real-time response is important, suspicious data will need to be transmitted quickly. This requires processing on the phone to threshold the signal strength to more than a certain number of standard deviations (say four) above the mean value of the signal.� However, our experiments suggest no more sophisticated processing than that is necessary on the phone, since this should provide a large data reduction, and the collection point can provide more sophisticated analyses like that detecting footstep sequences.� To reduce collection overload, phones need only transmit time and peak height since peak width did not appear important in our preliminary experiments.
If the sensors are deployed in a manner when they overlap, it may be beneficial to send all sensor data to the base station. This way anomalies detected by multiple phones can be correlated and give a better overall picture the location of the anomaly. This would reduce the computations on the phone but would require a constant Bluetooth stream to be transmitted, raising concerns on power consumption.
Acknowledgements
This research was partially supported by the National Science Foundation under grant 0729696.� The views expressed are those of the authors and do not reflect the policy of U.S. Government.
References
[1] Apple, Inc., �IPhone OS reference library�.� Retrieved March 1 from developer.apple.com: http://developer.apple.com/iphone/library/documentation (2010).
[2] ST Micro Electronics, MEMS Motion Sensor, retrieved Feb 26 from www.st.com: http://www.st.com/stonline/products/literature/ds/12726.pdf (2008).
[3] Sabatier, J., and Ekimov, A., �A Review of Human Signatures in Urban Environments Using Seismic and Acoustic Methods," Proc.� IEEE Conf.� on Technologies for Homeland Security, 215-220 (2008).
[4] Kavanagh, J. J., �Lower Trunk Motion and Speed-Dependence During Walking,� Journal of NeuroEngineering and Rehabilitation Vol 6, Issue 1, (2009).
[5] Ketcham, S., Anderson, T., Lacombe,J., and Moran, M., "Seismic propagation from humans in open and urban terrain," Proc.. IEEE Users Group Conference, 270-277 (2005).
[6] Rowe, N., Reed, A., and Flores, J., �Detecting suspicious motion with nonimaging sensors,� Proc.� Third IEEE International Workshop on Bio and Intelligent Computing, Perth, Australia, (2010).
[7] United States Marine Corps, [FMFM 6-4],� Washington D.C.: United States Navy,204 (1978).
[8] United States Marine Corps, �[MCWP 3-11.2],� Quantico: Department of the Navy,5-1 (1988).
Figure 7: Example deployment of phones in terrain with
potential concealment of adversaries.