MAST - Malicious Activity Simulation Tool
September 2012
| Contact: | Prof. Gurminder Singh or LtCol (Ret) John H Gibson |
| Dept of Computer Science | |
| Naval Postgraduate School | |
| Monterey, CA 93943 | |
| gsingh@nps.edu or jhgibson@nps.edu
|
| Students:
|
|
| CDR Will Taff, USN (Sept 2011) | |
| LCDR Paul Salevski, USN (Sept 2011) | |
| LT Justin Neff, USN (Mar 2012) | |
| CAPT Ray Longoria, USMC (Sept 2012) | |
| CDR Jim Hammond, USN | |
| LCDR Aaron Littlejohn, USN (Sept 2013, expected) | |
| LT Ehab Makhlouf, USN (Sept 2013, expected) | |
| LTJG Nat Hayes,
USN (Jun 2013, expected)
|
| Engineering Staff: | |
| Arijit Das | |
| Greg Belli | |
| Eric Lowney
|
MAST - Malicious Activity Simulation Tool - is a DoT&E sponsored project which aims to
support the conduct of network administrator security training on the very
network that the administrator is supposed to manage. A key element of MAST is
to use malware mimics to simulate malware behavior. Malware mimics look and
behave like real malware except for the damage that real malware causes.
The DoD currently employs
Red Teams to conduct network infiltration and security training for network
administrators. While red teams provide the most effective training, there are
several inherent constraints (limited availability, high expense, inconsistent
training and feedback) associated with the use of red teams for training
network administrators. MAST addresses these shortfalls by providing automated
and simulated actions of a red team that are realistic, repeatable, modular,
and dynamic. MAST is safe and designed to work on the trainees' operational
network.
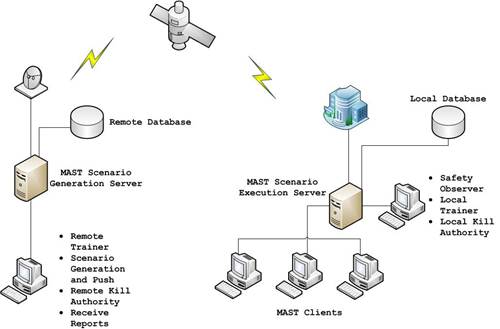
MAST is a client-server system and uses malware
mimics to enable simulated adversaries (red teams) and trusted agents (blue
teams) to leverage their existing skill sets, and conducts training without an
increase in risk while operating within the prescribed limits. Malware mimics
used in MAST allow for realistic and observable training of Network
Administrators on live, operational networks. Malware mimics are programs that are inherently stable and controllable,
but when activated, can produce the desired behaviors of a computer-based
network threat. Because malware mimics
are safe to use, they can be used effectively for training on live computer
networks.
MAST is currently under development. The
following activities are ongoing:
- Scenario Development and Testing - Develop
a library of scenarios and evaluate their interaction with Host-Based Security
System (HBSS)
- Scalability Testing - Determine how MAST
uses system and network resources
- Enhanced Capabilities - Developing dynamic roll-back script that will return the end host to its pre-training state.
